Reporting
Artifacts
What is it?
Artifacts track potential indicators of compromise and other notable events occurring throughout an operation.
Where is it?
A list of all current artifacts can be found by clicking the fingerprint icon at the top of Mythic.

How to use it?
This page tracks all of the artifacts automatically created by executing tasks. This should provide a good idea for both defenders and red teamers about the artifacts left behind during an operation and should help with deconfliction requests.
When is it updated?
Artifacts are created in a few different ways:
A command's tasking automatically creates an artifact.
An agent reports back a new artifact in an ad-hoc fashion
MITRE ATT&CK
What is it?
MITRE ATT&CK is a knowledge base of adversary tactics and techniques mapped out to various threat groups. It provides a common language between red teams and blue teams when discussing operations, TTPs, and threat hunting. For Mythic, this provides a great way to track all of the capabilities the agents provide and to track all of the capabilities so far exercised in an operation.
For more information on MITRE ATT&CK, check out the following:
Where is it?
MITRE ATT&CK integrations can be found by clicking the chart icon from the top navigation bar.

How to use it?
There are a few different ways to leverage this information.
Commands by ATT&CK
Clicking the "Fetch All Commands Mapped to MITRE" action will highlight all of the matrix cells that have a command registered to that ATT&CK technique. Clicking on a specific cell will bring up more specific information on which payload type and which command is mapped to that technique. All of this information comes from the MITRE ATT&CK portion of commands.

Tasks by ATT&CK
This is a slightly different view. This button will highlight and show the cells that have been exercised in the current operation. A cell will only be highlighted if a command was executed in the current operation with that ATT&CK technique mapped to it.

The cell view will show the exact command that caused the cell to be highlighted with a link (via task number) back to the full display of the task:

If there is an issue with the mapping, clicking the red X button will remove the mapping.
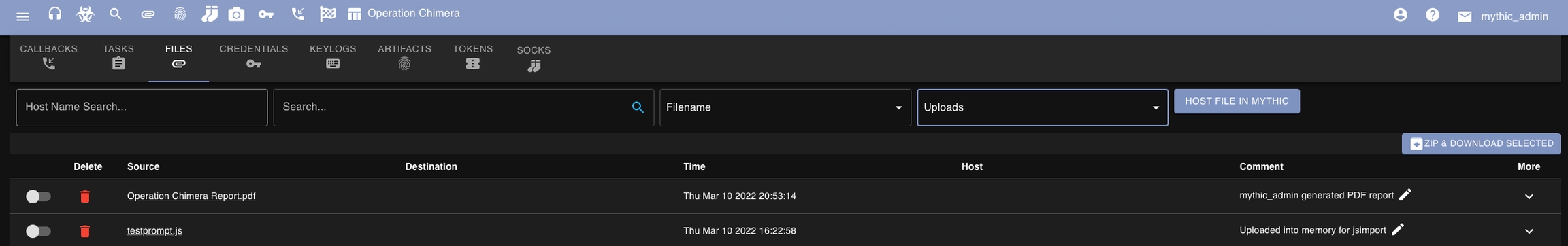
Reports
What is it?
Mythic can generate JSON or XML style reports. If you need a PDF version, simply generate the XML, open it up locally, and then in your browser save it off to PDF.
Where is it?
Report generation is located from the checker flag icon from the top navigation bar.
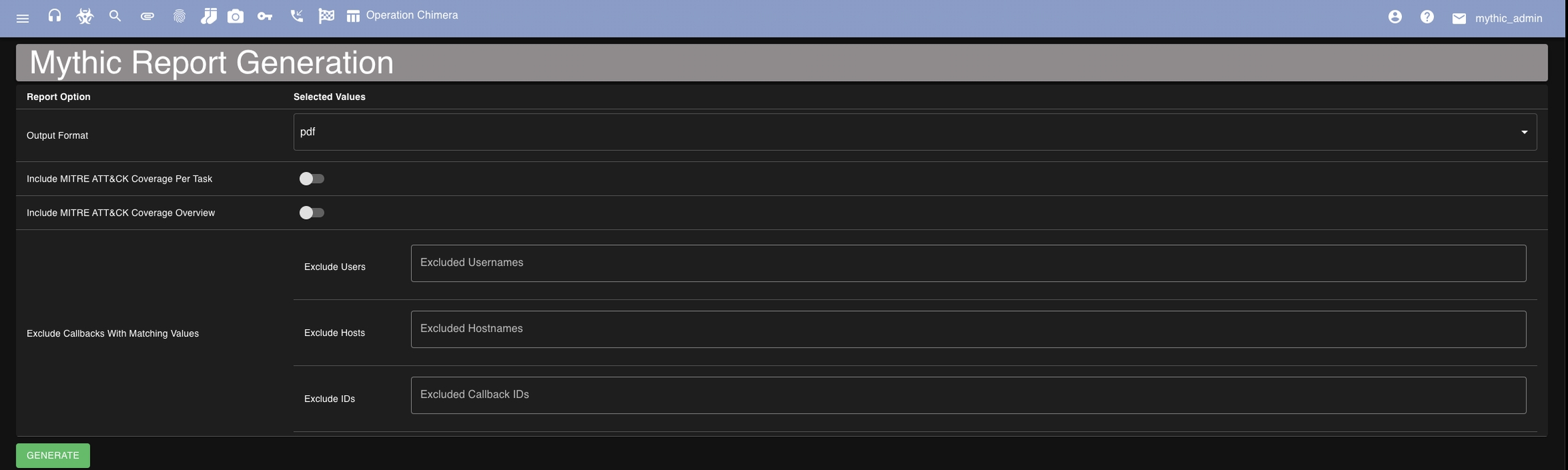
How to use it?
You can select your output format, if you want to include MITRE ATT&CK mappings inline with each tasking and if you want a MITRE ATT&CK Summary at the end. You can also optionally exclude certain callbacks, usernames, and hostnames from being included in the generated report.
The final generated report can be downloaded from this screen when it's ready via a toast notification. If you navigate away before it's done though, the report is also always available from the "files" section of the search page (click the paper clip icon at the top and select "Uploads" instead of "Downloads").