Auth Structure
Auth containers allow you to extend Mythic’s login capabilities by offloading the check from Mythic’s salted + hashed database password to something else. This can either be towards an Identity Provider (IDP) like Microsoft ADFS (SSO), or towards a non-identity provider/SSO check (like attempted auth to an LDAP service).Go Example
Auth Functionality
There are two forms of auth containers - Identity Provider (IDP) SSO Services and Non-IDP checks. The IDP and NonIDP Services are available as options in the Logon UI page as long as the containers are online. If the auth container goes offline, then the option will disappear from the Logon page and you will have to fallback to the normal Mythic logon procedures.IDP SSO Services
In these cases we are going to use the auth container to forward Mythic to a remote, SSO Identity Provider. This tends to have a few components:- The SSO Identity Provider needs to get some sort of metadata from the auth container to register it as a trusted partner (i.e.
GetIDPMetadata) - The user needs to be redirected to this IDP to kick off the auth flow (username/password, MFA, duo prompts, etc) (i.e.
GetIDPRedirect) - After the IDP has determined if you’re authorized or not, the result needs to be POSTed back to Mythic (and thus to the auth container) (i.e.
ProcessIDPResponse). The end result here has to return a message back to Mythic to inform Mythic of two things:
- was the authentication successful or not
- what is the email associated with the user that just authenticated
IDPServices array identifies which options are displayed to the user when they try to log in:
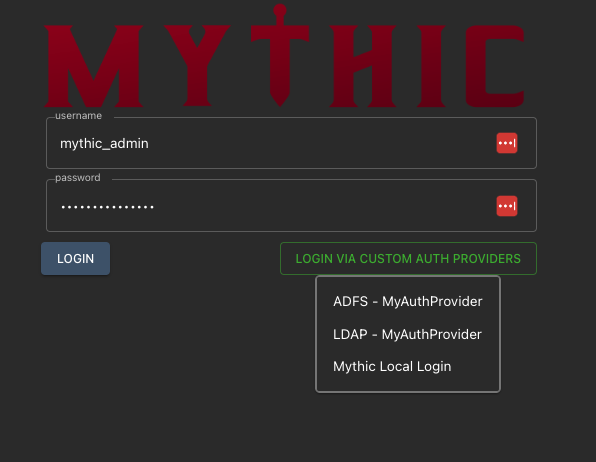
ADFS - MyAuthProvider kicks off a request to the GetIDPRedirect function.
Non-IDP SSO Services
The flow here is almost exactly the same as the IDP SSO Services, but instead of IDP, we have NonIDP everywhere. However, since we’re not redirecting the user to an SSO service, we need to specify what information we need the user to provide. TheGetNonIDPRedirect returns an array of fields that we want the user to specify:
username, password, and OTP. Once the user provides their data and click “login”, then the containers ProcessNonIDPResponse function is called.
Just like in the IDP SSO Services function, at the end of this we need to return if auth was successful or not and the email of the user that was authenticated.