What is it?
MITRE ATT&CK is a knowledge base of adversary tactics and techniques mapped out to various threat groups. It provides a common language between red teams and blue teams when discussing operations, TTPs, and threat hunting. For Mythic, this provides a great way to track all of the capabilities the agents provide and to track all of the capabilities so far exercised in an operation. For more information on MITRE ATT&CK, check out the following:Where is it?
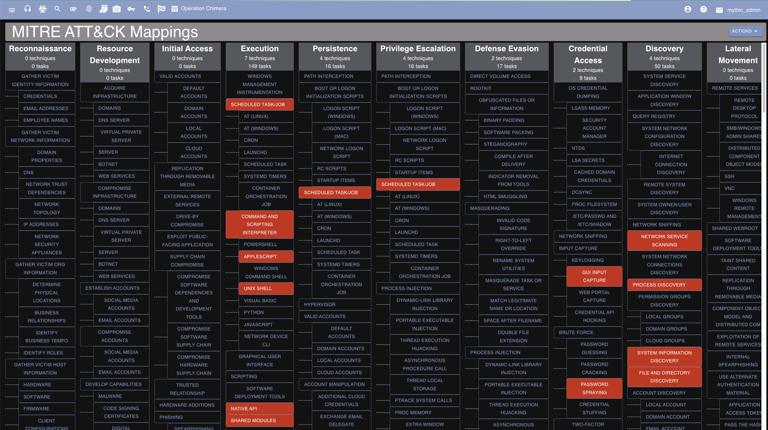
MITRE ATT&CK integrations can be found by clicking the chart icon from the top navigation bar.
How to use it?
There are a few different ways to leverage this information.Commands by ATT&CK
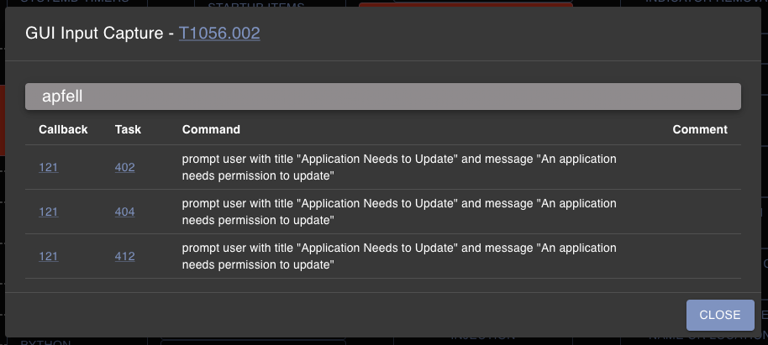
Clicking the “Fetch All Commands Mapped to MITRE” action will highlight all of the matrix cells that have a command registered to that ATT&CK technique. Clicking on a specific cell will bring up more specific information on which payload type and which command is mapped to that technique. All of this information comes from the MITRE ATT&CK portion of commands.
Tasks by ATT&CK
This is a slightly different view. This button will highlight and show the cells that have been exercised in the current operation. A cell will only be highlighted if a command was executed in the current operation with that ATT&CK technique mapped to it.